Petroleum Zones


With the industry's vulnerability scanning software, we analyze your entire network and devices to identify potential hidden cyber threats and security weaknesses; then recommend solutions to fix the vulnerabilities found.
Network Scanning To:
Identified potential threats are classified according to their threat’s levels.
Detected threats and their impacts are thoroughly evaluated
Your infrastructure and devices can be prioritized according to criticality.
Proffer solutions to remediate threats and vulnerabilities.
A copy of the scanned result is sent to client.
The detailed scanned report (with solution) can be used by the clients’ IT department to correct the weaknesses on the scanned network and devices. We are available to discuss the results.

With the industry's vulnerability scanning software, we analyze your entire network and devices to identify potential hidden cyber threats and security weaknesses; then recommend solutions to fix the vulnerabilities found.
What is Vulnerability Management?
process to identify, assess, report on, manage, and remediate “Cyber Vulnerabilities” across systems and assets.
ongoing practice of identifying, grouping, prioritizing, remediating, and mitigating software vulnerabilities (whether in the cloud or on-premises).
What is Vulnerability Assessment?
“Secure Your Assets & Infrastructure with us, Today”
We conduct “Vulnerability Assessment” scan to detect threats in your IT Assets and Devices.
With one of the best “Vulnerability Assessment” software, we scan and identify potential cyber threats and vulnerabilities that might, hiddenly, affect (and on its way to breach) data on your personal/company’s computer systems, Network Systems; or IT Infrastructure Systems and Assets.
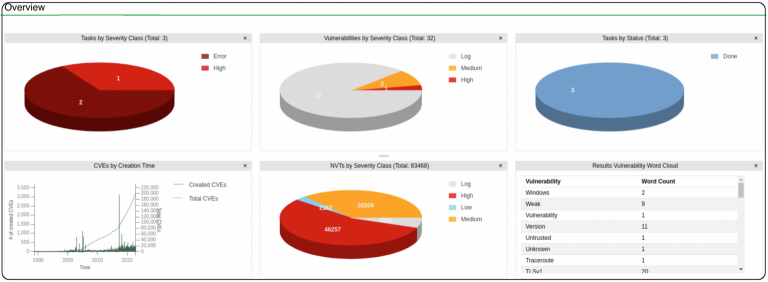
Detailed Reports (Results) – a copy would be sent to you.
The “Scanned Vulnerabilities Report” Would Include: